Description
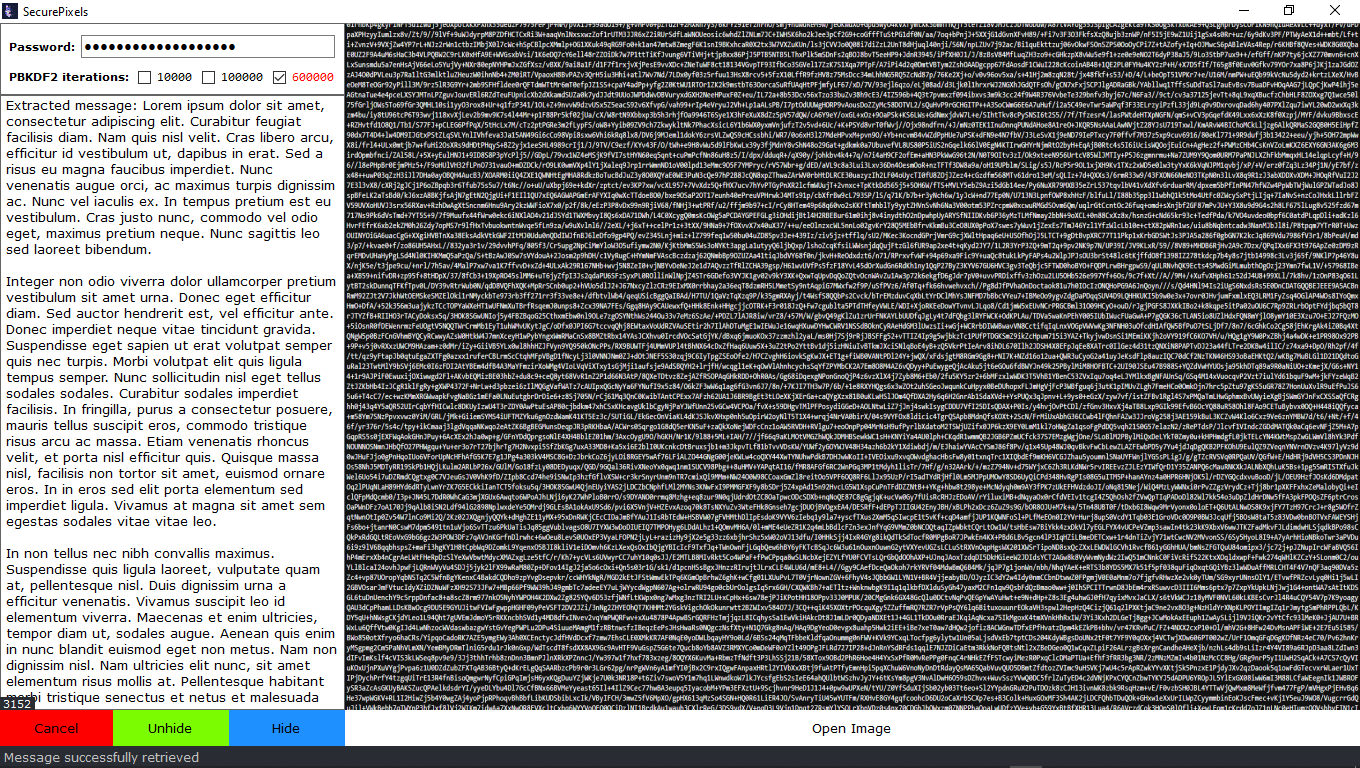
SecurePixels is a steganography tool that allows you to hide encrypted text within an image.
Steganography is another way we can confidentially transmit a message or store personal data by hiding it within other content.
Steganography is necessary for those who cannot afford to be suspected of hiding something.
– AES encryption
Uses AES-256 with PBKDF2 key derivation
The message is encrypted before being hidden
Even with access to the image, it cannot be read without the password
– Robust validation
File existence verification
Message size control (5000 character limit)
Image format validation
Automatic calculation of required vs. available capacity
– Uncompressed BMP and PNG format
Supported pixel format verification
Perfect preservation of modified bits
– Random distribution
Pseudo-random position generation based on the password
Uses all 3 RGB channels (triple capacity)
Reproducible seed for consistent extraction
– Multi-channel RGB
Uses Red, Green, and Blue channels
Triple capacity compared to the original
Equal distribution across all channels
– Enhanced security
Size limit on extracted data (protection against attacks)
Informative error messages without revealing sensitive information
Clean exception handling
– Plus features
Display of percentage of capacity used
Detailed progress messages
Cryptographic robustness analysis:
Mathematical complexity of encryption
AES-256: 2^256 = 1.15 × 10^77 possible keys
Comparison: More than the number of atoms in the observable universe (≈ 10^82)
PBKDF2 10,000 iterations: Multiplies each attempt time by 10,000
Brute force decryption time
Computing PowerKeys/second Time for AES-256
Home PC10^63.7 × 10^63 years
Supercomputer10^153.7 × 10^54 years
Theoretical quantum computer10^183.7 × 10^51 years
Realistic attack scenarios
Dictionary attack
Vulnerability: Weak passwords
PBKDF2 protection: 10,000 iterations make each test 10,000× slower
Recommendation: Passwords > 12 characters with complexity
Password brute force attack
8-char password (a-z,A-Z,0-9): 62^8 = 2.18 × 10^14 possibilities
With PBKDF2 10k: 2.18 × 10^14 × 10,000 = 2.18 × 10^18 operations
Estimated time (modern GPU): ~69,000 years
Advanced cryptanalytic attacks
Current state: No known vulnerabilities in AES-256
NSA/Agencies: No public evidence of AES-256 compromise
Time horizon: Security estimated until 2050+ minimum
Real protection in case of discovery
- If an attacker discovers your image with hidden message:
- Bit extraction → Incomprehensible encrypted data
- Pattern analysis → Uniform cryptographic noise
- Encryption identification → AES visible but unbreakable
- Password attack → Protected by PBKDF2
- Result → Message completely inaccessible
Comparison with military/government standards
- [NATO SECRET Standard] AES-256 encryption ⟹ SecurePixels Equivalent
- [NSA Suite B Standard] AES-256 + SHA-256 encryption ⟹ SecurePixels Compliant
- [FIPS 140-2 Standard] AES + PBKDF2 encryption ⟹ SecurePixels Compatible
Security conclusion
Even with steganography 100% compromised:
Decryption probability: 12 chars, complex)
No system compromise during encryption
No voluntary password disclosure
Cryptography constitutes your true protection, steganography being only an additional layer of obscurity. This is exactly the right security model!